ez_asm
众所周知 ChatGPT 可以看懂汇编,接下来有请二号选手下场解题。根据提供的汇编代码,我们可以还原出大致的 C 语言代码如下:
1 |
|
上述 C 代码大致还原了汇编代码的逻辑。现在,我们可以编写 Python 代码来进行逆运算,给定输入或一个字符串,将其反向操作以获得原始 Flag。
1 | def reverse_flag(flag): |
这段 Python 代码执行了与汇编代码中相反的操作,对给定的输入字符串进行逆运算以获得原始 Flag。运行后得到 Flag:flag{It_is_als0_impor@nt_t0_13arn_4sm!}
easy_re
它都说是 easy 了你就相信它一回吧:
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
不难看出其中唯一一个处理步骤是把每个字符的高 4 位和低 4 位交换了,所以直接给它交换回来就是了:
1 | des = '66 C6 16 76 B7 45 27 97 F5 47 03 F5 37 03 C6 67 33 F5 47 86 56 F5 26 96 E6 16 27 97 F5 07 27 03 26 C6 33 D6 D7'.split() |
所以 Flag:flag{Try_t0_s0lv3_the_binary_pr0bl3m}
seed
直接开动态调试把内存扒出来,剩下的自己算:
1 | cipher = [bytes.fromhex(char)[0] for char in "40 29 28 e9 c2 04 a4 ed 9f 53 5f 75 3c d1 cd 2b a8 c4 89 69 15 21 16 ef d7 27 92 df ca 53 5f 2a 3c d1 ce 03 a3 ef a5 78 16 1a 2d e1 c4".split()] |
所以 Flag:flag{Give_y0u_the_se3d_and_D0_you_w@nt_t0_do}
easy_math
先解方程:
1 | from sympy import symbols, Eq, solve |
然后拼一下 Flag:
1 | from Crypto.Util.number import long_to_bytes |
所以 Flag:flag{N0_One_kn0ws_m@th_B3tter_Th@n_me!!!!}
ez_apk
Android 逆向什么的不会啊怎么办?直接拆 APK 包拿到 classes3.dec 丢进 IDA,代码不多直接看
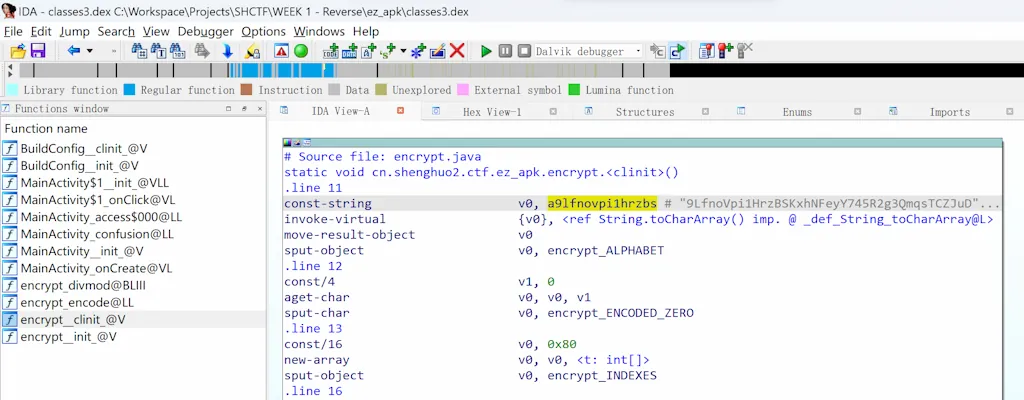
encrypt 这边应该是实现了一个自定义字母表的 Base58,然后还找到了一个 secret,直接去尝试解码:
1 | def base58_decode(encoded_str): |
运行后得到 Flag:flag{Jue_1_ju3_Y0ung_and_G0at_1s_go0d_for_yOuR_body}
not gcc
题目给了一个 bc 文件,这是 LLVM IR bitcode 文件,属于编译过程中产生的一个文件,直接让 clang 继续编译就能得到可执行文件。
反编译后看了眼,是个 Sudoku:
1 | sudoku = [4, 0, 7, 0, 0, 3, 2, 0, 8, |
先想点办法把这个数独给解决了:
1 | solved = [4, 9, 7, 5, 1, 3, 2, 6, 8, |
然后按程序的逻辑合成下 Flag:
1 | for i in range(81): |
pycode
这么长一串 Disassembly 我可不看,直接丢给 ChatGPT 让它尝试去还原一下 Python 代码:
1 | import base64 |
肉眼可见有一大串没什么用的代码,直接顺手写一个逆运算:
1 | import base64 |
运行后得到 Flag:flag{1b36920e-c180-b250-6537-30238f5}
Authur's_box
先反编译为伪代码:
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
不难看出 byte_408A80 与 Str2 异或的结果便是 Flag。Str2 可以直接在 IDA 里拿到,然后通过动态调试拿 byte_408A80 的值:
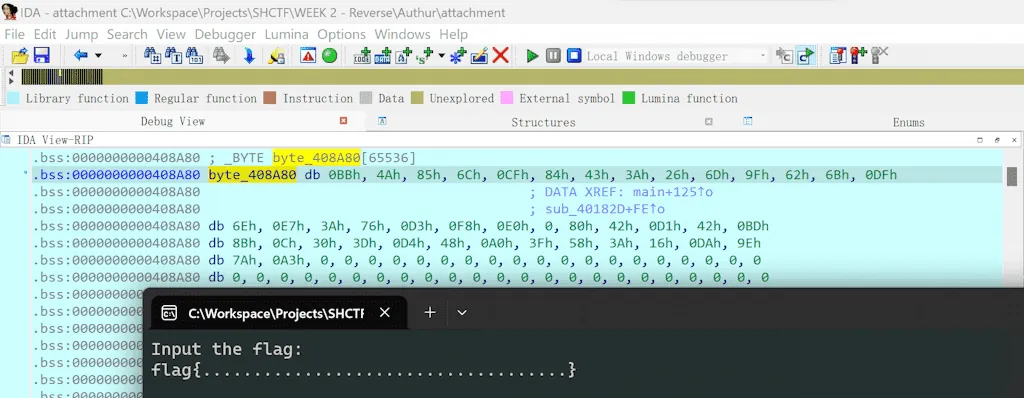
然后编写脚本:
1 | string1 = [0xDD, 0x26, 0xE4, 0x0B, 0xB4, 0xE2, 0x20, 0x0B, 0x10, 0x5D, |
得到 Flag:flag{fc160a07-f6c7-4b3a-87fd-b12318a3d0bb}
easyre
1 | % ./easyre.exe |
由此可见这是个 Python 脚本打包得到的程序,使用工具解包得到 pyc 文件,然后再反编译得到 Python 代码:
1 | import base64 |
不难编写出下面的程序计算出 xor_key 值为 23:
1 | import sympy as sp |
那么解一下 Marshal:
1 | import base64 |
阅读 Disassembly 后大致可以得知其内部使用一个 rc4_encrypt 函数,将输入的内容用一个 key 加密后与 check 变量比对。RC4 的解密函数即为加密函数,直接把 check 用相同的 key 丢进 rc4_encrypt 跑一遍就能得到 Flag 了。本来想打算直接:
1 | code_obj = marshal.loads(decoded_data) |
但是一直 Segmentation Fault,最后选择另抄 rc4_encrypt 函数:
1 | def rc4(key, data): |
得到 Flag:flag{d8e8d9d0-b2b1-7304-74b760-90b11ab6a3}
crackme
1 | % file crackme |
直接先 Lua 反编译:
1 | print("please input your flag:") |
剩下的直接交给 Python 怎么暴力怎么来:
1 | secret = [None, 54, 57, 566, 532, 1014, 1, 7, 508, 10, 12, 498, 494, 6, 24, 14, 20, 489, 492, 0, 10, 490, 498, 517, 539, 21, 528, 517, 530, 543, 9, 13, 0, 4, 51, 562, 518, 526, 512, 525, 522, 60, 573, 61, 575, 574, 0, 518, 513, 41, 31, 1, 594, 117, 15] |
运行后得到 Flag:flag{C000ngr4tulat1ons!Y0u_Cr4cked_m3_9c2be68a76f9!!!}
This article is authored by luoingly and is licensed under CC BY-NC 4.0
Permalink: https://luoingly.top/post/shctf-2023-reverse-writeup/