world.execute.me
意义不明。
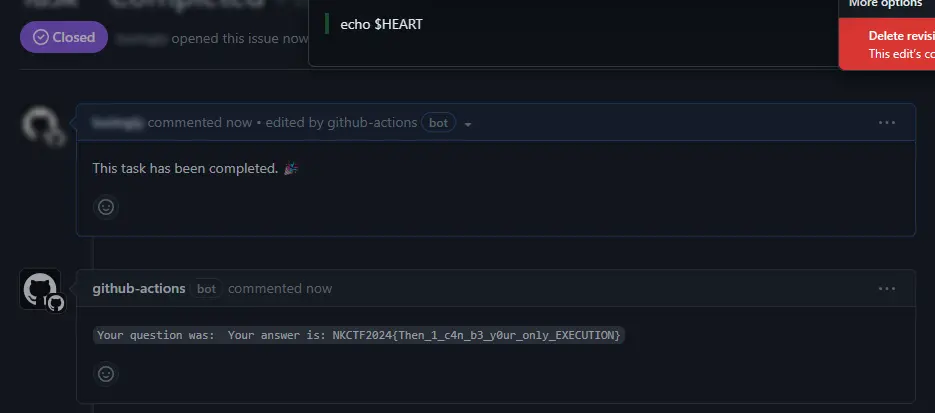
注意到 ANSWER=$(echo '${{ github.event.issue.body }}' | grep -vP 'Question:.*$'),解析到的内容会被运行然后返回。经过测试只要 Issue 内容不包括 Question: 那么 ANSWER 捕获到的就是整个 Issue body,所以直接 Payload: echo $HEART。
Webshell_pro
HTTP 的返回包是仅 Base32、Base64 编码,没有额外加密,直接用 Wireshark 把各个包抓下来解码一下,可以得到一个 Python 代码以及:
1
2
3
4
| FLAG is NOT HERE!!!!!!!!!!!
PASSWORD:
Password-based-encryption
|
怀疑 Python 代码就是 HTTP 请求 Payload 的加密代码,自己手搓一下解密部分:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
| import base64
import libnum
from Crypto.PublicKey import RSA
prikey = """-----BEGIN PRIVATE KEY-----
MIICdgIBADANBgkqhkiG9w0BAQEFAASCAmAwggJcAgEAAoGBAIr+q/k/yLFaOgUjavMXra2bqwMWdGwqwaFVIK7FAjG56ExZAua/pM/HJNA958gq5/N9QVpxr9geQhUgLX2iGYTlfvfxO3EZs6CIZ5/hu932xTozjaTy8yUI8mnXCgMUM4WgFCmvhjMfhlNHo+z4c/xUQgkwbm6ItA4vF0p3GLjVAgMBAAECgYBDsqawT5DAUOHRft6oZ+//jsJMTrOFu41ztrKkbPAUqCesh+4R1WXAjY4wnvY1WDCBN5CNLLIo4RPuli2R81HZ4OpZuiHv81sNMccauhrJrioDdbxhxbM7/jQ6M9YajwdNisL5zClXCOs1/y01+9vDiMDk0kX8hiIYlpPKDwjqQQJBAL6Y0fuoJng57GGhdwvN2c656tLDPj9GRi0sfeeMqavRTMz6/qea1LdAuzDhRoS2Wb8ArhOkYns0GMazzc1q428CQQC6sM9OiVR4EV/ewGnBnF+0p3alcYr//Gp1wZ6fKIrFJQpbHTzf27AhKgOJ1qB6A7P/mQS6JvYDPsgrVkPLRnX7AkEAr/xpfyXfB4nsUqWFR3f2UiRmx98RfdlEePeo9YFzNTvX3zkuo9GZ8e8qKNMJiwbYzT0yft59NGeBLQ/eynqUrwJAE6Nxy0Mq/Y5mVVpMRa+babeMBY9SHeeBk22QsBFlt6NT2Y3Tz4CeoH547NEFBJDLKIICO0rJ6kF6cQScERASbQJAZy088sVY6DJtGRLPuysv3NiyfEvikmczCEkDPex4shvFLddwNUlmhzml5pscIie44mBOJ0uX37y+co3q6UoRQg==
-----END PRIVATE KEY-----
"""
prikey = RSA.import_key(prikey)
def dec_replace(base64_str: str):
base64_str = base64_str.replace("e5Lg^FM5EQYe5!yF&62%V$UG*B*RfQeM", "/")
base64_str = base64_str.replace("n6&B8G6nE@2tt4UR6h3QBt*5&C&pVu8W", "+")
base64_str = base64_str.replace("JXWUDuLUgwRLKD9fD6&VY2aFeE&r@Ff2", "=")
base64_str = base64_str + '=' * (4 - len(base64_str) % 4)
return base64_str
def decrypt(cipher_text, d):
cipher_text = base64.b64decode(dec_replace(cipher_text).encode())
plain_text = b""
for i in range(0, len(cipher_text), 128):
part = cipher_text[i:i+128]
dec = libnum.n2s(pow(libnum.s2n(part), d, n))
plain_text += dec
return plain_text
if __name__ == '__main__':
from Crypto.Util.number import inverse
phi = (int(prikey._p) - 1) * (int(prikey._q) - 1)
d = inverse(int(prikey.d), phi)
import urllib.parse
cipher = urllib.parse.unquote(input().strip())
plain = decrypt(cipher, d)
print(plain)
|
用 Wireshark 抓点流量出来解解,能够找到:
1
2
| G1TUg4bIVOFYi8omV2SQrTa8fzYfboRNN7fV6FJn6%26B8G6nE%402tt4UR6h3QBt%2A5%26C%26pVu8Wbm3O74uCUbwMkvRCYae44TX1ZO8X4w2Nk1igaIZjSQIJ9MMHhD9cn6%26B8G6nE%402tt4UR6h3QBt%2A5%26C%26pVu8WSV5EzikNsyM5c1nlPS8uqw1P2pJuYLaLxloK0x5xhQHDqqAxkuKrBzPn0noQ2bDn6%26B8G6nE%402tt4UR6h3QBt%2A5%26C%26pVu8WlVnGwsfP7YP9PYJXWUDuLUgwRLKD9fD6%26VY2aFeE%26r%40Ff2
b'echo U2FsdGVkX1+SslS2BbHfe3c4/t/KxLaM6ZFlOdbtfMHnG8lepnhMnde40tNOYjSvoErLzy0csL7c5d4TlMntBQ== > /root/FLAG/flag.txt'
|
用上面得到的密码将其解密(OpenSSL AES)就得到了 Flag。
ctf80
这几种语言的 Polyglot 能找到现成的代码。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| #
#include <stdio.h>
#ifdef __cplusplus
char msg[5] = {'C', 'a', 'i', 'n', '\n'};
#else
char msg[9] = {'c', 'r', 'a', 'z', 'y', 'm', 'a', 'n', '\n'};
#endif
int main() { int i; for(i = 0; i < 9; ++i) putchar(msg[i]); return 0;}
|
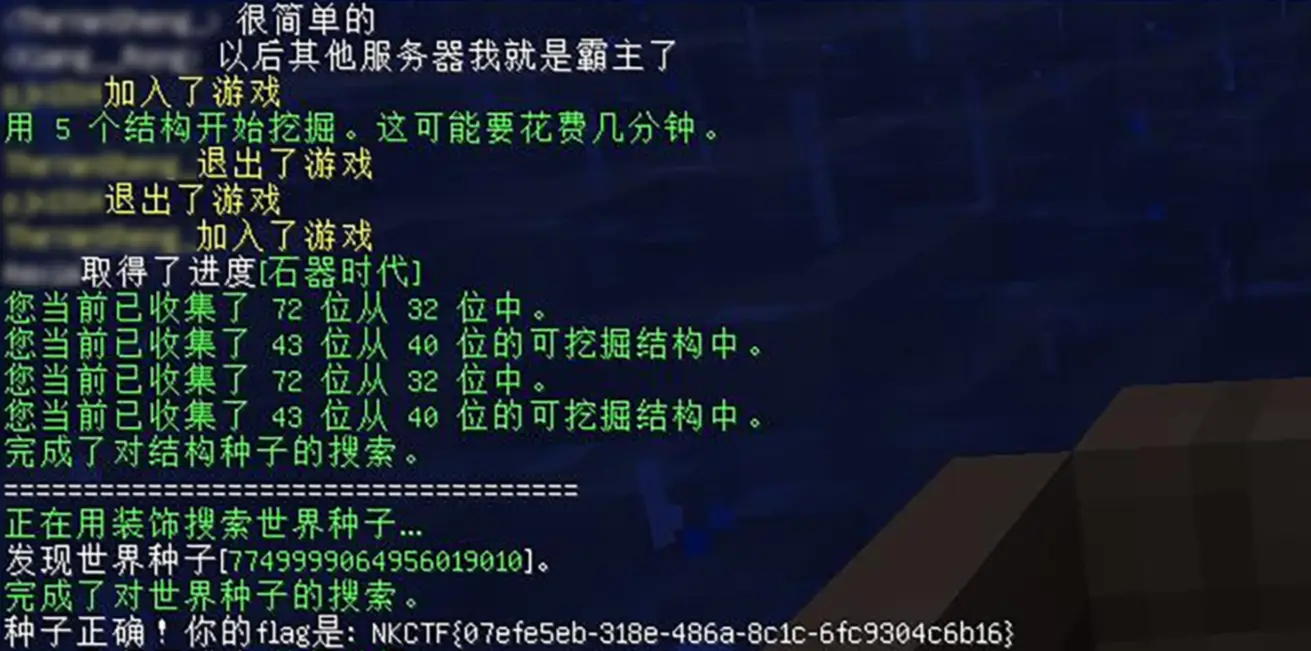
Minecraft:SEED
进入 Minecraft 服务器查看后得知,该题只需要得到服务器当前地图的种子便可以得到 Flag。在没有权限的情况下,可以使用一些工具利用建筑物的坐标来破解种子。某个服务器早些时候地图出生点附近就是海,直接造船出海然后沿着海岸线跑图,用不了多久就能得到所需要的东西: