crackme
Crack 什么 Crack 啊,直接运行就行了。
babyRe
这题为什么不放在 Crypto,咱甚至没去看那个可执行文件。
1 | p+q= |
众所周知:
1 | (p+1)\*(q+1) = p\*q + (p+q) +1 |
所以直接算 d 解:
1 | from Crypto.Util.number import long_to_bytes, inverse |
EasyRe
直接 IDA 启动,其逻辑并不复杂,就是看着哪里怪怪的:
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
单纯的异或,只不过对 B 和 X 有特殊处理。逆着算一下:
1 | cipher = "]P_ISRF^PCY[I_YWERYC" |
eazy_z3
1 | print("Please input flag:") |
别慌,直接用 sympy 求解:
1 | from Crypto.Util.number import long_to_bytes |
mfx_re
upx: 6
其实就是 UPX 壳,但是出题人把其中 UPX 的标识符改为了 MFX。将其修改回来就可以用 UPX 脱壳了。然后丢进 IDA 直奔主题:
1 | scanf("%s", s); |
不难解:
1 | cipher = 'HRBSEza63aa28d,bb62,3c40,7708,e`31c0d8acd7|' |
z3_revenge
上难度了。
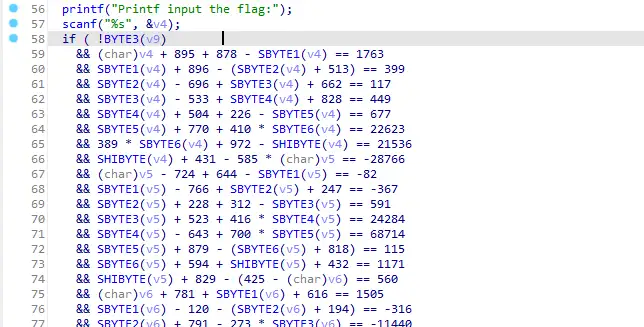
不过这又有什么问题呢?
1 | import re |
这个脚本可以把 IDA 反编译出来的伪代码转换为 sympy 需要的等式:
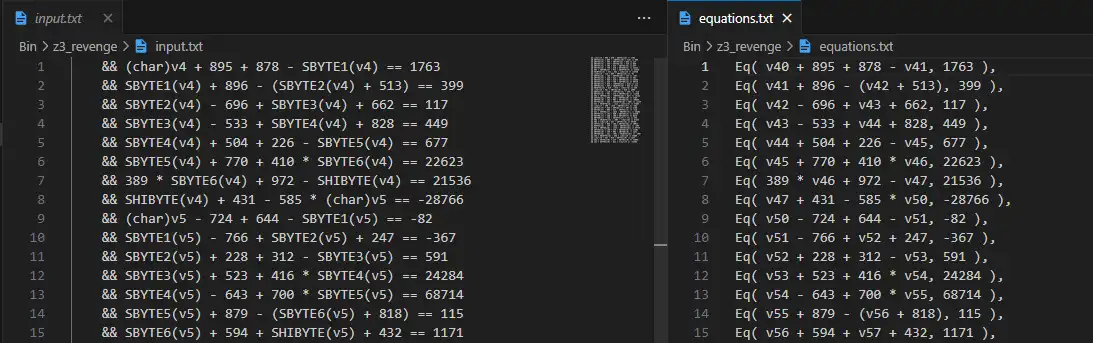
然后上 sympy!
1 | from sympy import symbols, Eq, solve |
This article is authored by luoingly and is licensed under CC BY-NC 4.0
Permalink: https://luoingly.top/post/isctf-2023-reverse-writeup/