有好一段时间没打比赛了。
本次随「Ciallo~(∠・ω< )⌒☆」队伍参赛,个人拿下了两道 Misc 题目的一血,还有一道题由于我太菜了,手慢无。
DigitalSignature
1 | from eth_account import Account |
stegh 小鬼
观察了一下 快乐小鬼 这个文件,貌似是一个 JPG,字节倒了高低位也倒了,先摆摆正:
1 | $ python -c "open('快乐小鬼.jpg', 'wb').write(bytes([(i % 16) * 16 + (i // 16) for i in open('快乐小鬼', 'rb').read()][::-1]))" |
有俩 JPG,拆一下:
1 | $ binwalk 快乐小鬼.jpg |
拿 ExifTool 看 second.jpg 在 XP Comment 那部分有「新佛曰:……」,但是这不重要了,因为给了如下 Hint:
1 | 新佛曰挂了,解码出来--pass:2333333 |
试了一下是 StegHide:
1 | $ steghide extract -sf second.jpg -p 2333333 |
得到的 pass.txt 里面参和了俩个东西,一个是 Base100,解码得到 This_1s_P4ssw0rd:
1 | 👋👟👠👪👖🐨👪👖👇🐫👪👪👮🐧👩👛 |
还有一坨是 aaEncode,解码得到 Look carefully at the middle of the picture:
1 | ゚ω゚ノ= /`m´)ノ ~┻━┻ //*´∇`*/ ['_']; o=(゚ー゚) =_=3; c=(゚Θ゚) =(゚ー゚)-(゚ー゚); (゚Д゚) =(゚Θ゚)= (o^_^o)/ (o^_^o);(゚Д゚)={゚Θ゚: '_' ,゚ω゚ノ : ((゚ω゚ノ==3) +'_') [゚Θ゚] ,゚ー゚ノ :(゚ω゚ノ+ '_')[o^_^o -(゚Θ゚)] ,゚Д゚ノ:((゚ー゚==3) +'_')[゚ー゚] }; (゚Д゚) [゚Θ゚] =((゚ω゚ノ==3) +'_') [c^_^o];(゚Д゚) ['c'] = ((゚Д゚)+'_') [ (゚ー゚)+(゚ー゚)-(゚Θ゚) ];(゚Д゚) ['o'] = ((゚Д゚)+'_') [゚Θ゚];(゚o゚)=(゚Д゚) ['c']+(゚Д゚) ['o']+(゚ω゚ノ +'_')[゚Θ゚]+ ((゚ω゚ノ==3) +'_') [゚ー゚] + ((゚Д゚) +'_') [(゚ー゚)+(゚ー゚)]+ ((゚ー゚==3) +'_') [゚Θ゚]+((゚ー゚==3) +'_') [(゚ー゚) - (゚Θ゚)]+(゚Д゚) ['c']+((゚Д゚)+'_') [(゚ー゚)+(゚ー゚)]+ (゚Д゚) ['o']+((゚ー゚==3) +'_') [゚Θ゚];(゚Д゚) ['_'] =(o^_^o) [゚o゚] [゚o゚];(゚ε゚)=((゚ー゚==3) +'_') [゚Θ゚]+ (゚Д゚) .゚Д゚ノ+((゚Д゚)+'_') [(゚ー゚) + (゚ー゚)]+((゚ー゚==3) +'_') [o^_^o -゚Θ゚]+((゚ー゚==3) +'_') [゚Θ゚]+ (゚ω゚ノ +'_') [゚Θ゚]; (゚ー゚)+=(゚Θ゚); (゚Д゚)[゚ε゚]='\\'; (゚Д゚).゚Θ゚ノ=(゚Д゚+ ゚ー゚)[o^_^o -(゚Θ゚)];(o゚ー゚o)=(゚ω゚ノ +'_')[c^_^o];(゚Д゚) [゚o゚]='\"';(゚Д゚) ['_'] ( (゚Д゚) ['_'] (゚ε゚+/*´∇`*/(゚Д゚)[゚o゚]+ (゚Д゚)[゚ε゚]+(゚Θ゚)+(゚Θ゚)+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+((゚ー゚) + (o^_^o))+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+((゚ー゚) + (o^_^o))+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(o^_^o)+(゚Д゚)[゚ε゚]+(゚ー゚)+(c^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+(o^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+(゚Θ゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+((o^_^o) - (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((o^_^o) +(o^_^o))+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (o^_^o))+(゚Θ゚)+(゚Д゚)[゚ε゚]+(゚ー゚)+(c^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+(゚Θ゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚ー゚)+(c^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(c^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚ー゚)+(c^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(゚Θ゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚ー゚)+(c^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+((゚ー゚) + (o^_^o))+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((o^_^o) +(o^_^o))+(゚Д゚)[゚ε゚]+(゚ー゚)+(c^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(c^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚ー゚)+(c^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+(c^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(゚Θ゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+(o^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+((o^_^o) - (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚o゚]) (゚Θ゚)) ('_'); |
试探了一下, 快乐小鬼.jpg 在两个 JPG 文件之间还有一串 Base64:
1 | $ tail first.jpg | strings -n 10 |
解压 ZIP 文件又得到了一堆 Emoji,丢进 emoji-aes 用 This_1s_P4ssw0rd 解密得到 Flag:
1 | DASCTF{Y0u_are_4_1ovely_Gh0st} |
Steganography_challenges0.2
题目给了一个 PNG 文件,在 IEND 之后还有一坨 Base64:
1 | $ tail Steganography_challenges0.2.png | strings -n 10 | base64 -d |
整个解密先:
1 | from Crypto.Cipher import ARC4 |
图片中间有一小块东西:
把那一小块单独截取出来看 LSB:
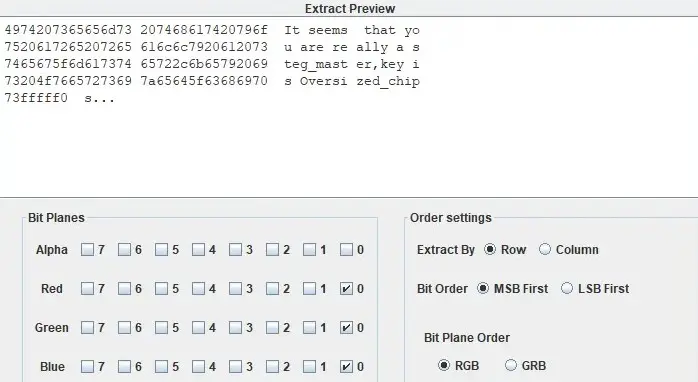
提取一下,还是一个 PNG:
1 | $ python cloacked-pixel-python3/lsb.py extract -i decrypted_image.png -o cloacked_pixel_decrypted.bin -p Oversized_chips |
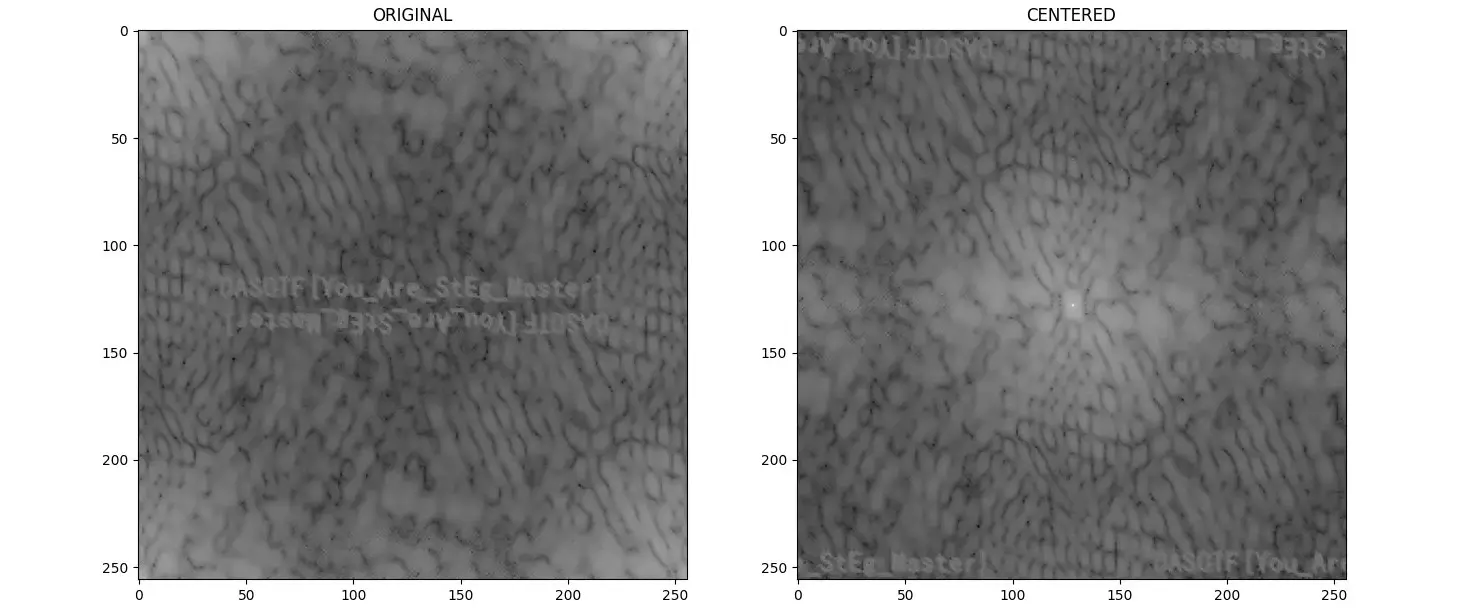
有频域水印:
SecretPhotoGallery
随便 Fuzz 一下登录框发现能注入,先用 ' union select 1, 1, 1; 让自己登录。下发了一个 JWT:
1 | eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyIjoiJyB1bmlvbiBzZWxlY3QgMSwgMSwgMTsiLCJyb2xlIjoiZ3Vlc3QiLCJpYXQiOjE3NjUwMDM4NjN9.0CTUd0AHDdVbmlPH3o44XSDSwP1xFRO857wlA7clyLg |
HTML 里有一堆一堆的注释,收集起来是 GALLERY2024SECRET:
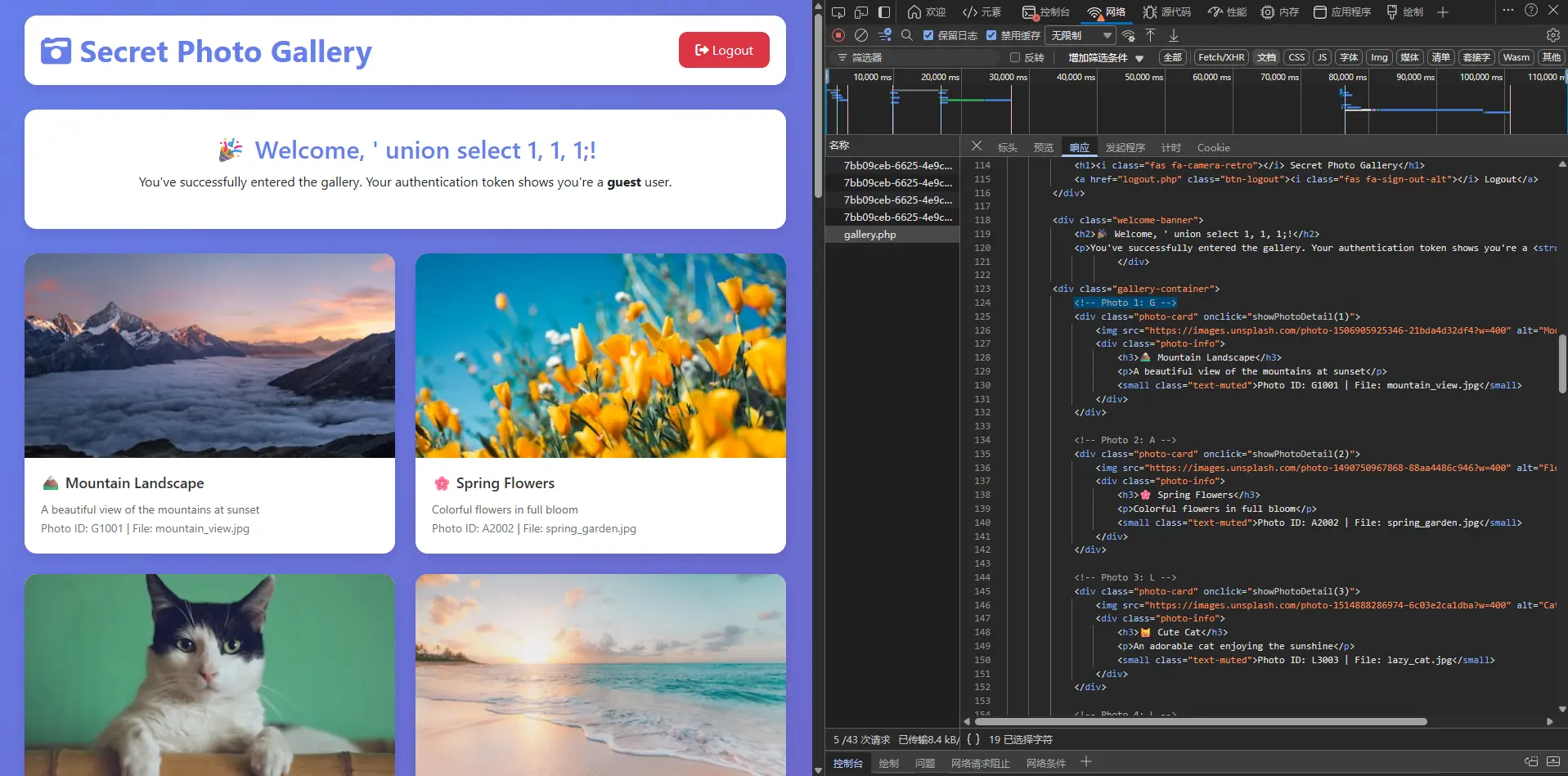
试了一下发现是 JWT 的 Secret,那给自己签个 admin 好了:
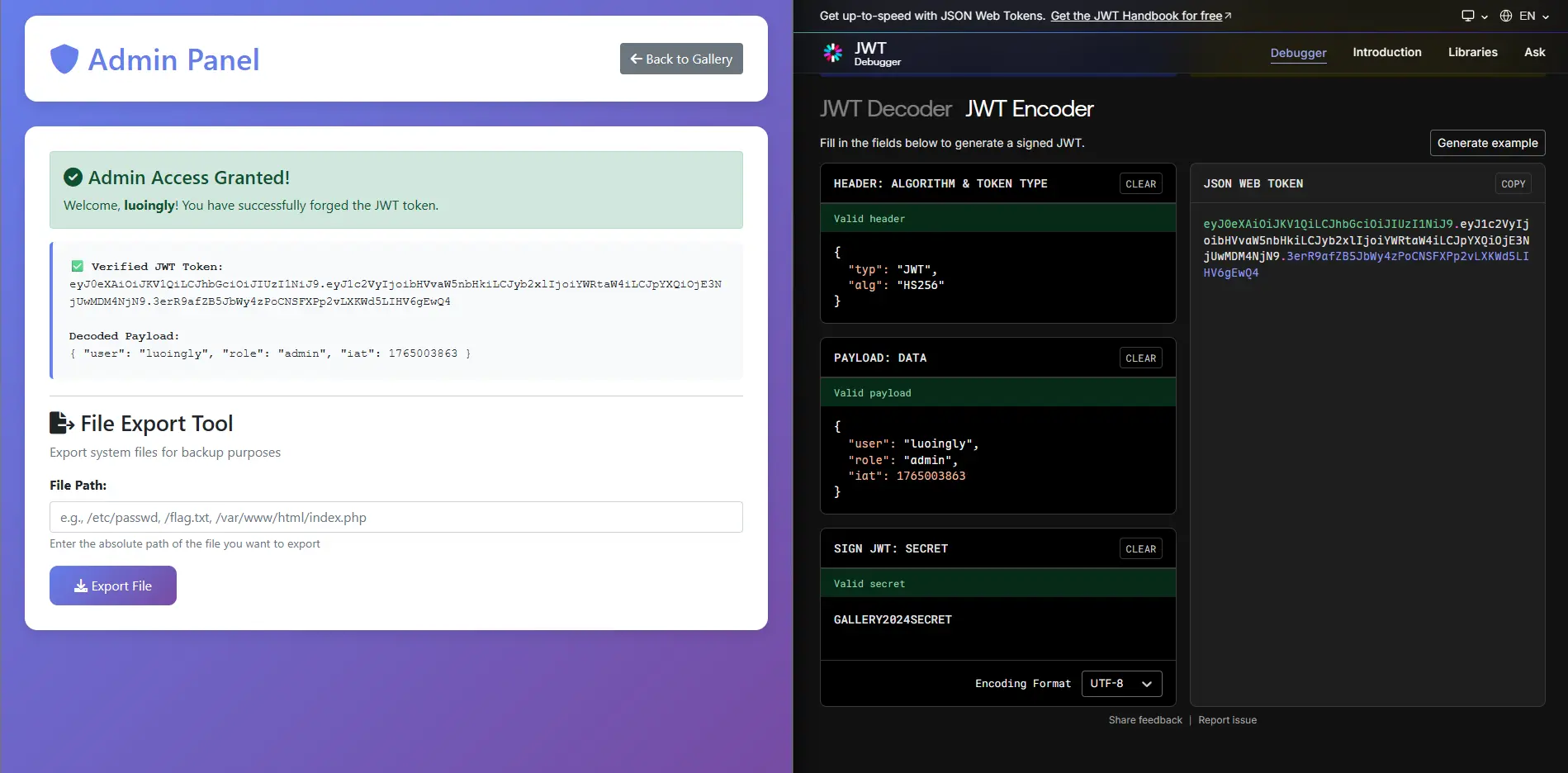
File Export 用的是 include ,尝试 php://filter 读 flag.php 发现把 base64 过滤了。问题不大:
1 | php://filter/convert.iconv.UTF-7.UCS-4/resource=flag.php |
devweb
不明所以的前端,请求直接往 localhost 发的。逆一下吧,一个带加密的登录,还有一个带签名的文件下载,尝试直接访问 /download?file=app.jmx&sign=6f742c2e79030435b7edc1d79b8678f6 被 500 了,还是先看看登录吧:
1 | import requests |
拿着这个 JSESSIONID 再去访问 /download?file=app.jmx&sign=... 能下载到一个 JMeter 测试计划文件,里面有 sign 的具体计算方式。手搓一下:
1 | import hashlib |
This article is authored by luoingly and is licensed under CC BY-NC 4.0
Permalink: https://luoingly.top/post/dasctf-2nd-half-2025-writeup/