古典密码
1 | AnU7NnR4NassOGp3BDJgAGonMaJayTwrBqZ3ODMoMWxgMnFdNqtdMTM9 |
猜测是 Base64,但是直接使用常用字母表无法正确解码,猜测还有前置步骤。尝试了常见古典加密方式后发现为 AtBash 埃特巴什码,转换后得到:
1 | ZmF7MmI4MzhhLTk3YWQtZTlmNzQzbGdiYjA3LWNlNDctNmUwMjgwNGN9 |
可以正常进行 Base64 解码,得到:
1 | fa{2b838a-97ad-e9f743lgbb07-ce47-6e02804c} |
判断为栅栏密码,解密后得到 flag:
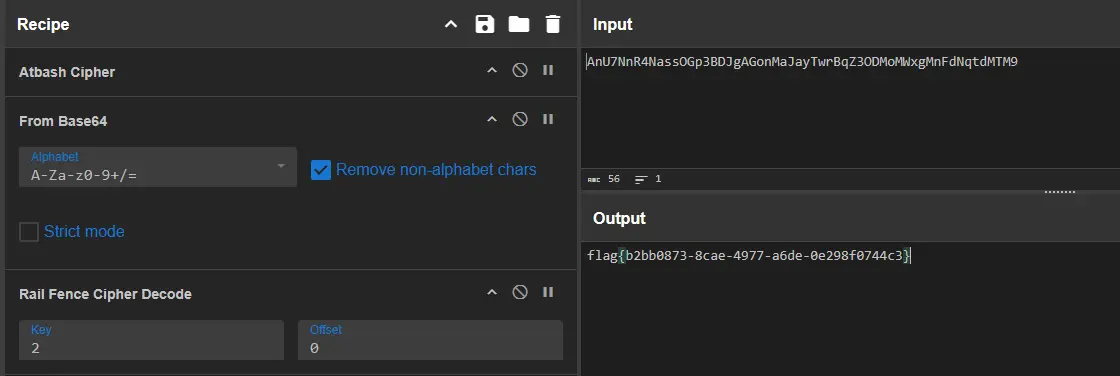
火锅链观光打卡
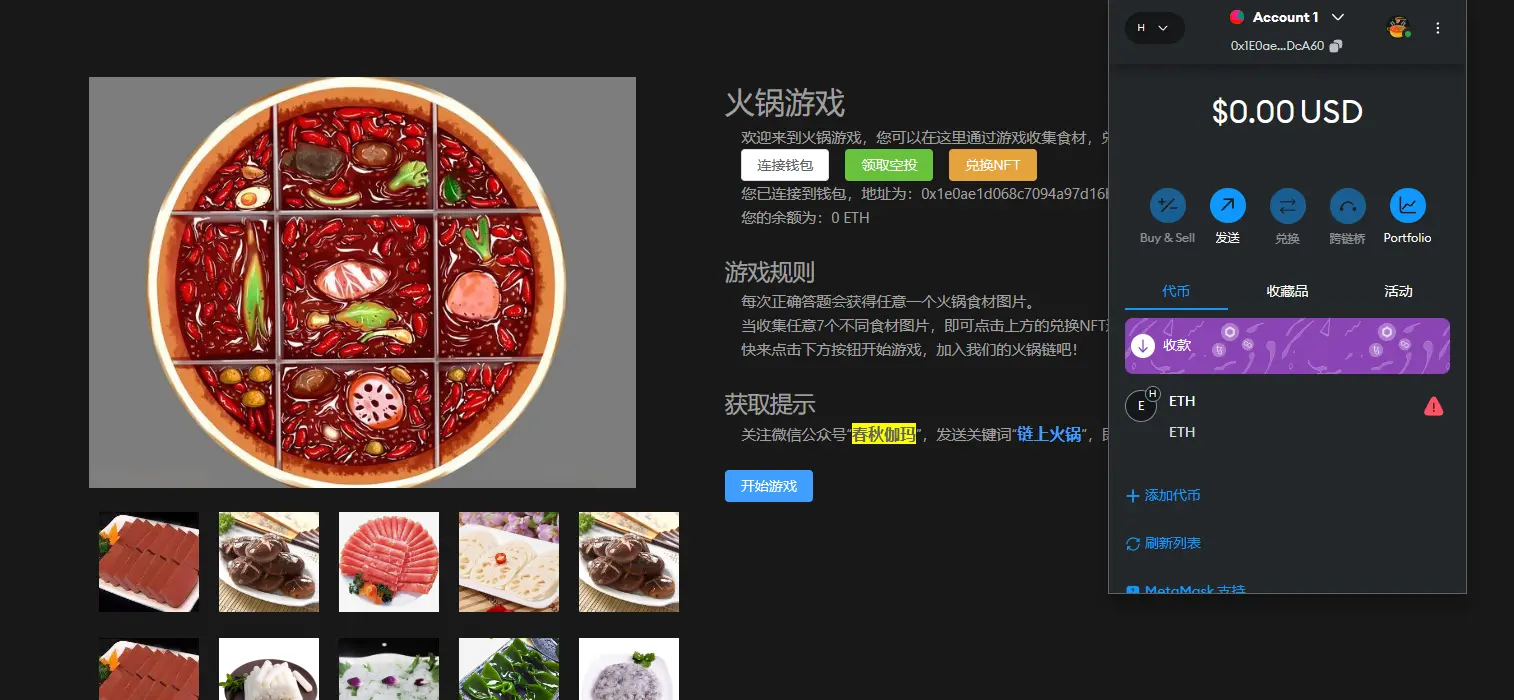
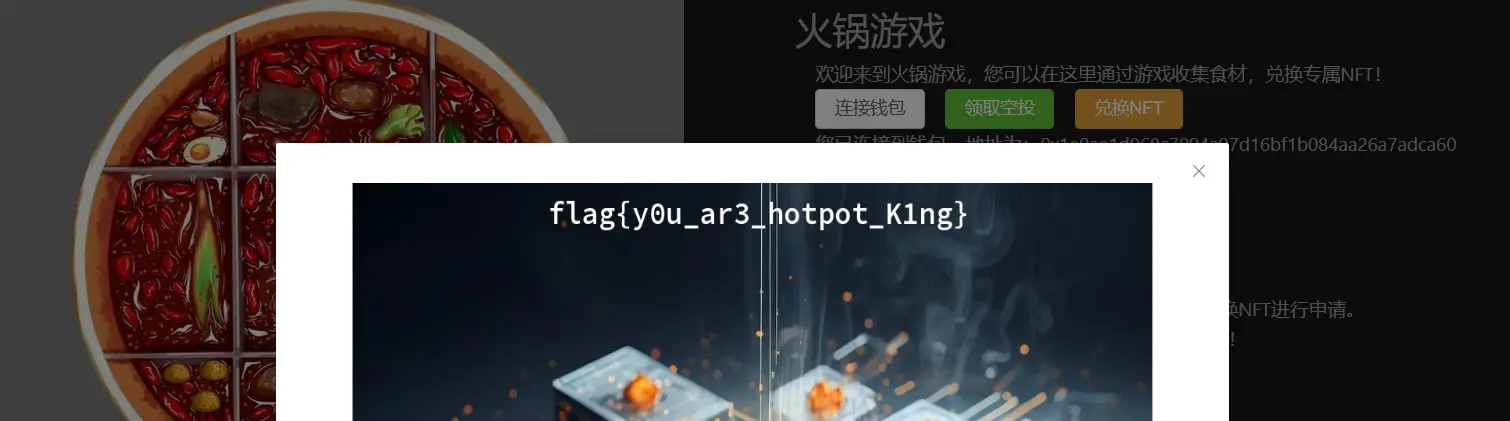
按照题目要求,在浏览器上安装 MetaMask 插件并创建一个钱包,然后通过网页连接到火锅链。领取空投后进行游戏,回答足够多的问题即可集齐所需的食材,兑换 NFT 即可获得 flag。
asm_re
从主函数往下跟可以发现变换部分,变换完后会和一组数据(unk_100003F10)进行比较:
1 | __text:0000000100003C7C loc_100003C7C; CODE XREF: _main+BC↑j |
由于前后字符互不影响,直接将所有可打印字符进行相应的处理后作为字典逆向查找解 flag:
1 | from string import printable |
This article is authored by luoingly and is licensed under CC BY-NC 4.0
Permalink: https://luoingly.top/post/ciscn-s17-quals-writeup/